When data being exchanged between two systems, receiver may request (the sender) to send Digital Signature along with the data.
In this writing, we will cover,
1. What is the benefit of sending Digital Signature, along with data.
2. How Digital Signature works.
What is the benefit of sending Digital Signature, along with data:
Assume that we (as a sender) needs to send the data "Bank Account Number 100" to the receiving system. Receiving system received the data, but they received it as "Bank Account Number 200", because some one changed the data during data transmission (using hacking).
How does the receiver know that the data is modified by some one, during the data transmission.
Receiver can verify this when we send Digital Signature along with the data.
Digital Signature is some value generated based on the data being transferred (encrypted hash value of data). Any minor change to the data will produce different Digital Signature.
When the data is transferred together with Digital Signature, receiver will verify if Digital Signature matches with the data or not. If the data is changed during transmission, Digital Signature will no longer match.
We might have a question, what if hacker changes data and also the Digital Signature (matching with modified data) during transmission. This is not possible because Digital Signature can not be generated without knowing Private Key used for Digital Signature generation.
How Digital Signature works:
In this writing, we will cover,
1. What is the benefit of sending Digital Signature, along with data.
2. How Digital Signature works.
What is the benefit of sending Digital Signature, along with data:
Assume that we (as a sender) needs to send the data "Bank Account Number 100" to the receiving system. Receiving system received the data, but they received it as "Bank Account Number 200", because some one changed the data during data transmission (using hacking).
How does the receiver know that the data is modified by some one, during the data transmission.
Receiver can verify this when we send Digital Signature along with the data.
Digital Signature is some value generated based on the data being transferred (encrypted hash value of data). Any minor change to the data will produce different Digital Signature.
When the data is transferred together with Digital Signature, receiver will verify if Digital Signature matches with the data or not. If the data is changed during transmission, Digital Signature will no longer match.
We might have a question, what if hacker changes data and also the Digital Signature (matching with modified data) during transmission. This is not possible because Digital Signature can not be generated without knowing Private Key used for Digital Signature generation.
How Digital Signature works:
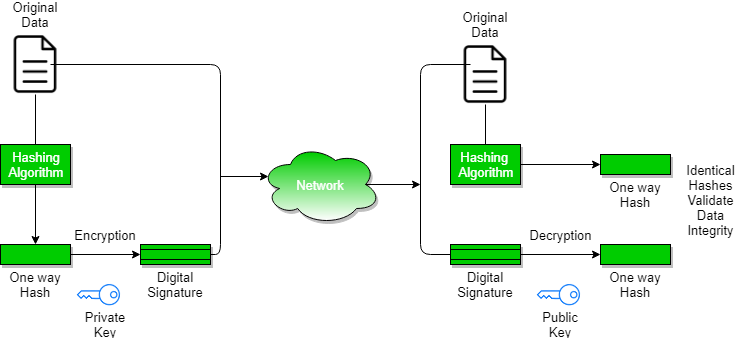
- Sender generates digital signature using following two major steps.
Generate 'One way Hash' based on data being transferred.
2. Signing
Encrypt the 'One way Hash' (calculated in step 1) with the Private Key.
The encrypted 'One way Hash' is called Digital Signature.
- Sender sends data along with digital signature.
- Receiver receives the data along with digital signature.
- Receiver verifies the data and signature, using following steps.
1. Generate 'One way Hash' based on data received.
2. Decrypt Digital Signature using the Public Key, to get 'One way Hash' sent by sender.
3. Now, 'One way Hash' calculated by receiver,
should match one-way Hash sent by sender.
